A potentially damning report from Israel-based cybersecurity firm Cyberint has revealed that Chinese state-sponsored advanced persistent threat (APT) group “Mustang Panda” conducted three cyber espionage campaigns against entities in the South Pacific, including the Philippine government, in August 2023.
The campaigns utilized legitimate software such as Solid PDF Creator and SmadavProtect, an Indonesian antivirus solution, to execute malicious files onto target systems.
The threat actors also devised a clever approach of cloaking the malware’s command and control communications to mimic legitimate Microsoft traffic, the report noted.
Mustang Panda is a Chinese APT group that has been operating since at least 2012. The group is believed to be affiliated with the Chinese government and has been linked to a number of cyberespionage campaigns targeting government entities, nonprofits, and other organizations in North America, Europe, and Asia.
On August 1, 2023, it was observed that a Mustang Panda malware package was hosted for download on Google Drive.
The threat actors had disguised the malware package as a ZIP file named 230728 meeting minutes.zip. When unsuspecting victims extracted the archive, they were presented with the figure below:
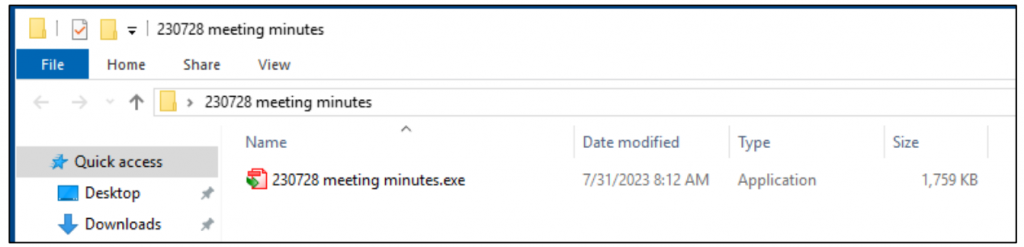
Upon opening the extracted folder, victims are presented with an application named “20230728 meeting minutes.exe” bearing a PDF icon. This file is a renamed copy of the legitimate Solid PDF Creator software.
However, unbeknownst to the victims, the folder also contains a hidden file named “SolidPDFCreator.dll.” Executing the seemingly harmless “20230728 meeting minutes.exe” triggers the side-loading of the malicious DLL residing in the same folder.
Once loaded, the malicious DLL communicates with 45.121.146[.]113 to establish a command-and-control (C2) connection.
“Our assessment indicates that an entity affiliated with the Philippine government encountered this initial malware package as early as August 1, 2023,” the Cyberint report said.
The third campaign, created on August 16, 2023, mirrored the structure of the first campaign. However, the ZIP and EXE filenames differ, with the third campaign using “Labour Statement.zip” instead of “230728 meeting minutes.zip” from the first instance.
Upon extracting the ZIP file’s contents, victims encounter two files. The first file, “Labour Statement.exe,” is a harmless copy of the Solid PDF Creator software. The second file, identified as “SolidPDFCreator.dll,” harbors malicious intent.
Executing the seemingly innocuous “Labour Statement.exe” triggers loading the malicious DLL residing in the same folder.
Subsequently, the malicious DLL establishes a connection with 45.121.146[.]113, mirroring the command-and-control (C2) communication pattern observed in the previous two campaigns.
Throughout August, Mustang Panda operatives orchestrated at least three cyber espionage campaigns directed at entities within the South Pacific region.
“Our assessment indicates that at least one of these campaigns specifically targeted the Philippine government, and the perpetrators successfully infiltrated a government agency for five days in August,” it said.
Cyberint said Mustang Panda consistently proved its effectiveness in carrying out persistent cyber espionage operations, establishing itself as one of the most active Chinese APT groups.
These operations target a diverse range of entities worldwide that align with the geopolitical interests of the Chinese government, it added.
“We strongly urge organizations to utilize our findings to inform the implementation of protective measures to counter this threat group,” it concluded.




