On average, it took less than a day — approximately 16 hours — for attackers to reach Active Directory (AD), one of the most critical assets for a company, a report from cybersecurity firm Sophos said.
Sophos recently released its Active Adversary Report for Tech Leaders 2023, an in-depth look at attacker behaviors and tools during the first half of 2023.
AD typically manages identity and access to resources across an organization, meaning attackers can use AD to easily escalate their privileges on a system to simply log in and carry out a wide range of malicious activity.
“Attacking an organization’s Active Directory infrastructure makes sense from an offensive view. AD is usually the most powerful and privileged system in the network, providing broad access to the systems, applications, resources and data that attackers can exploit in their attacks. When an attacker controls AD, they can control the organization. The impact, escalation, and recovery overhead of an Active Directory attack is why it’s targeted,” John Shier, field CTO, Sophos, said.
“Getting to and gaining control of the Active Directory server in the attack chain provides adversaries several advantages. They can linger undetected to determine their next move, and, once they’re ready to go, they can blast through a victim’s network unimpeded.
“Full recovery from a domain compromise can be a lengthy and arduous effort. Such an attack damages the foundation of security upon which an organization’s infrastructure relies. Very often, a successful AD attack means a security team has to start from scratch.”
The report further said that median attacker dwell time — the time from when an attack starts to when it’s detected — shrunk from 10 to eight days for all attacks, and to five days for ransomware attacks.
In 2022, the median dwell time decreased from 15 to 10 days.
The dwell time for ransomware attacks also declined. They were the most prevalent type of attack in the IR cases analyzed, accounting for 69% of investigated cases, and the median dwell time for these attacks was just five days.
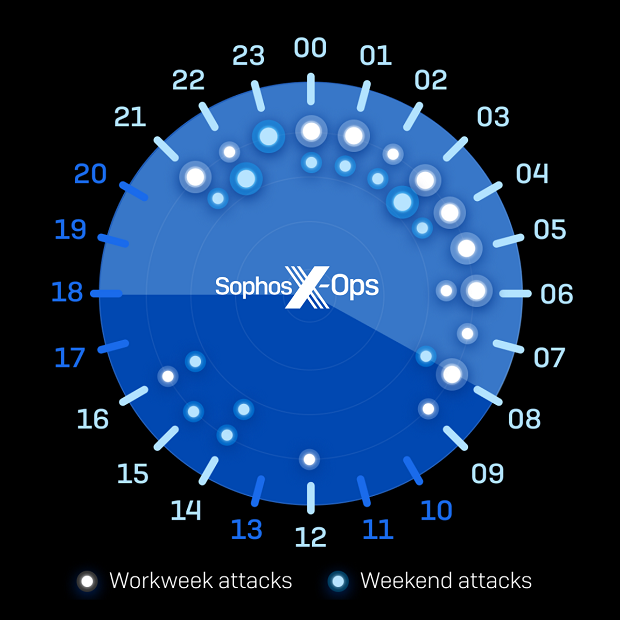
In 81% of ransomware attacks, the final payload was launched outside of traditional working hours, and for those that were deployed during business hours, only five happened on a weekday.
The number of attacks detected increased as the week progressed, most notably when examining ransomware attacks. Nearly half (43%) of ransomware attacks were detected on either Friday or Saturday.
“In some ways we’ve been victims of our own success. As adoption of technologies like XDR and services such as MDR grows, so does our ability to detect attacks sooner. Lowering detection times leads to a faster response, which translates to a shorter operating window for attackers,” Shier said.
“At the same time, criminals have been honing their playbooks, especially the experienced and well-resourced ransomware affiliates, who continue to speed up their noisy attacks in the face of improved defenses,” he added.